Subdomain Brute Forcing Leads to Admin Access in the Navy
This post is about my first valid and critical bug on HackerOne in 2023 where I utilized different kind of recon techniques to end up getting admin access.
Dorking #
While Google Dorking for navy.mil, I encountered results with minimal content. So I tried searching with DuckDuckGo, where I used the query site:navy.mil git to search for Git files.
Despite the limited results I received from DuckDuckGo, there was one domain in particular that stood out to me.
gitlab.devops.nswccd.navy.mil
Brute Forcing #
I started to brute force subdomains with ffuf because I figured that there’d be more subdomains within the DevOps domain since DevOps usually contains various development, testing, and deployment subdomains.
I brute forced using Assetnote’s best-dns.txt wordlist, which I often use for brute forcing subdomains. I ran the command below in my TMUX session:
ffuf -u https://FUZZ.devops.nswccd.navy.mil -w /opt/wordlists/assetnote/best-dns-wordlist.txt
I used a tool that I wrote for concatenating the subdomains from ffuf with the main subdomain provided:
./domain-retriever.py -d devops.nswccd.navy.mil -f ffuf-output.txt
The result:
gitlab.devops.nswccd.navy.mil
jira.devops.nswccd.navy.mil
jenkins.devops.nswccd.navy.mil
artifactory.devops.nswccd.navy.mil
Admin Access #
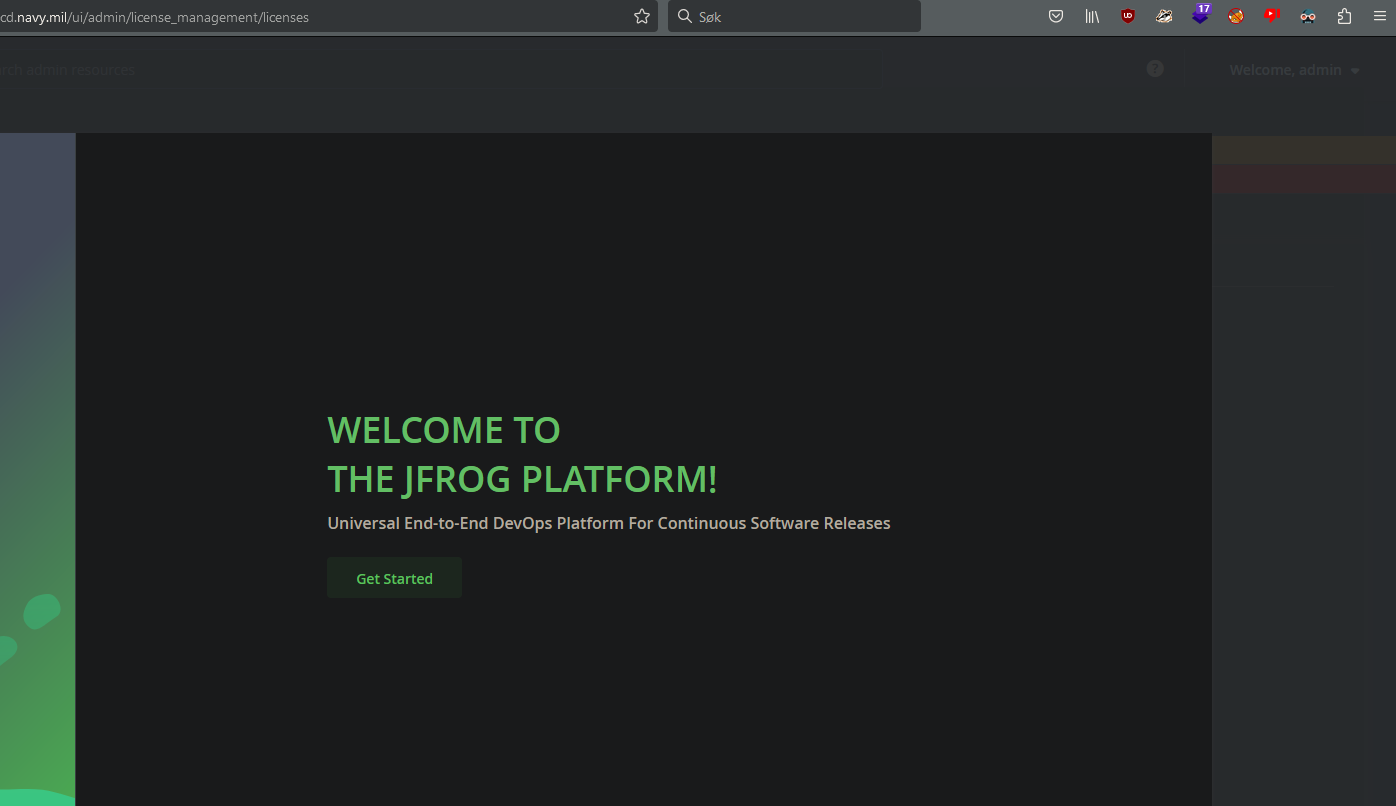
The “artifactory” subdomain hosted a JFrog login page. I started looking for any JFrog CVEs, but had no luck there. Many systems come preconfigured with default credentials, so I googled for JFrog’s default credentials. To my surprise, the site had default credentials, which were “admin:password”. I managed to gain admin access.
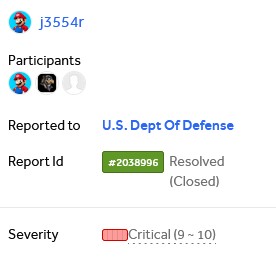
The vulnerability was accepted, marking my first valid and critical finding on HackerOne, and to the U.S. Department of Defense.