Abusing the PUT method on Drexel University
This post explains how I exploited the HTTP PUT method to upload and overwrite files on a web application for user authentication.
I noticed that Drexel University awards letters to individuals who discover vulnerabilities in their web applications, so I decided to find vulnerabilities to receive their letter.
Detecting the Vulnerability #
During my reconnaissance efforts, I noticed an interesting subdomain via Shodan. It was an old looking login page for Drexel University. I used the OPTIONS method to see which HTTP methods were supported. Several methods were allowed, and the one that caught my eye was the PUT method. This method allows anyone to upload any file to the webserver root, and overwrite any file as well.
Exploitation #
The simple PUT request below uploads a file named “xss.html” to the web server. The body of the request contains JavaScript code that triggers an alert displaying the message “Test” whenever the page is visited:
PUT /xss.html HTTP/1.1
Host: m3labdatafed.mem.drexel.edu
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) Gecko/20100101 Firefox/127.0
Content-Type: text/plain
<script>alert("Test")</script>
This could allow attackers to steal sensitive user information such as login credentials, or inject harmful code into webpages by customizing the code.
For example, by using the PUT method, entering a filename and file content into the HTTP body, then sending my request, I managed to upload a Proof of Concept login page to demonstrate the severity of this vulnerability:
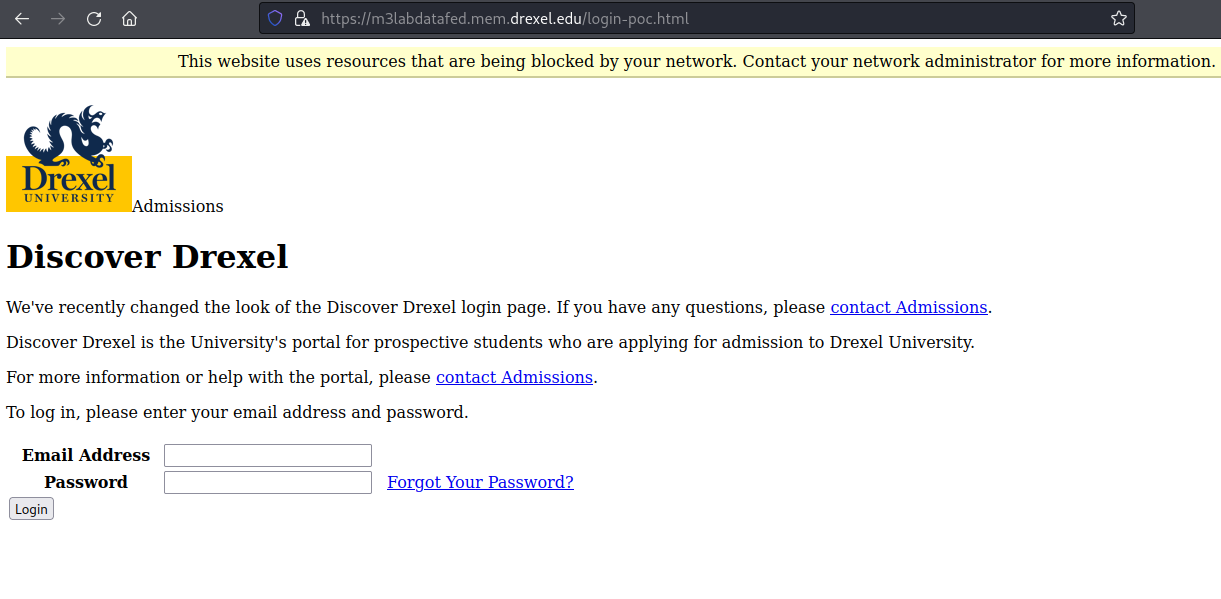
I responsibly reported the vulnerability to their security team. In response, they immediately disabled the vulnerable domain and awarded me a letter of recognition for my contribution:
